Fake Celebrity-Endorsed Bitcoin Scam Abuses Ad Tech to Net $1M in 1 Day
FizzCore — The Engine of Deception

Sad Day, Tragedy Strikes, The World is In Shock
(Sampler of FizzCore banner ads in various countries)
Today we’re uncovering an attacker that sits at the increasingly blurred boundary between malvertising and deceptive ads. FizzCore — as we’ve called this threat actor, has perfected the art of audit circumvention to exploit the gullibility of aspiring cryptocurrency investors.
We’re presenting the result of 6 months of research, covering August 2019 to January 2020 but we could trace back the presence of the underlying scam through 2018 on a wide range of attack vectors (email spam, Facebook, banner ads and native ads on news sites, Google search).
At an age where online marketing and social media can be manipulated to skew perception of reality at scale, here’s an attacker who’s able to defeat traditional digital advertising QA mechanisms to reach millions of visitors with a highly lucrative scam.
A new type of malvertising attack
FizzCore is a significant newcomer in the malvertising landscape. Despite not relying on forced redirects, FizzCore implements techniques to successfully evade ad quality reviews and persist:
- Cloaking (fake ad creatives and fake landing pages hiding real payload).
- Reputation and relationship building in the ad ecosystem (8 ad platforms, 3 ad servers in 6 months).
- Carefully crafted localized campaigns using celebrity endorsement clickbait.
The space that FizzCore trades in is high scale / high impact similar to Tech Support Scams. Cryptocurrency scamming is a $3B business according to the FTC. Each campaign draws thousands of victims each losing thousands of dollars to the perpetrators. So much so that the backlash resulted in 2 lawsuits against Facebook and many police complaints from celebrities falsely endorsing the scam.
Our research shows how FizzCore exploits ad tech to cash in on a binary trading bitcoin scam operation that has been active for multiple years.
The scam behind the scam
We found multiple landing pages presenting a Bitcoin investment opportunity under multiple brand names and localized to the targeted geography. The various services (“Bitcoin Trader”, “Bitcoin Evolution”, “Bitcoin Future”, “Bitcoin Code”, “Bitcoin Era” and many more) all follow the same UI and theme, and all contain the same fine print in the footer of the page:
Important Risk Note: Trading binary options can generate significant benefits but also involves a risk of partial or full funds loss […]
A “Binary option” is an exotic form of investment with a binary outcome (earn a fixed amount or lose your investment). The general consensus is that binary option investment opportunities are extremely risky and prone to scams. Investigative reporter Simona Weinglass is widely regarded as an expert in the field. She has spent the last few years investigating the boom of binary option scams, which has grown to become an estimated $3B industry in 2018 according to the FTC.
In the case of this Bitcoin investment scam, after submitting their contact information, would-be investors are contacted by a sales representative and sold on the opportunity. Any funds invested are irremediably lost.
Visitors are funneled to these scams by networks of affiliates who advertise for these “offers” with deceptive tactics on social media, banner ads on news sites, or email spam.
Journalist Eric Van den Berg exposed (in Dutch) the ecosystem of celebrity-endorsed Bitcoin scam affiliates. To drive visitors to fake Bitcoin investments, affiliates typically earn $600 per conversion while the scammers make an average $3,000 per victim, Van de Berg reported. The day to day of these Bitcoin scam operations is made of hard-sell pitches to collect so-called investments from victims.
Our research started after Eric reached out to us in June of last year, looking for any feedback on his own findings on celebrity-endorsed bitcoin scams, especially on Facebook in the Netherlands.
Things slowly started to fall in place from there. In August, we spotted a suspicious campaign with unusual cloaking behaviors. From September, reports of the celebrity-endorsed banner ads started trickling in in the UK, in November it turned to Germany and Italy.
Introducing FizzCore, a large scale affiliate with global reach that uses cloaked deceiving ads to maximize persistence and maximize click-through rates.
A World of Celebrities

In each of FizzCore’s target countries, their impact generated public outcry. Victims of the scheme have been found in the UK [1, 2, 3, 4, 5], in Germany [1, 2, 3], Spain [1, 2, 3, 4], Netherlands [1], Italy, France [1], Australia [1, 2, 3].
Notably, the scammers have avoided the US probably for fear of harsh legal consequences.
The Usual “Conversion” Flow and The Twist
We present below the general flow that brings victims all the way down to making an “investment”. This classic affiliate marketing flow comes with a few “twists”.
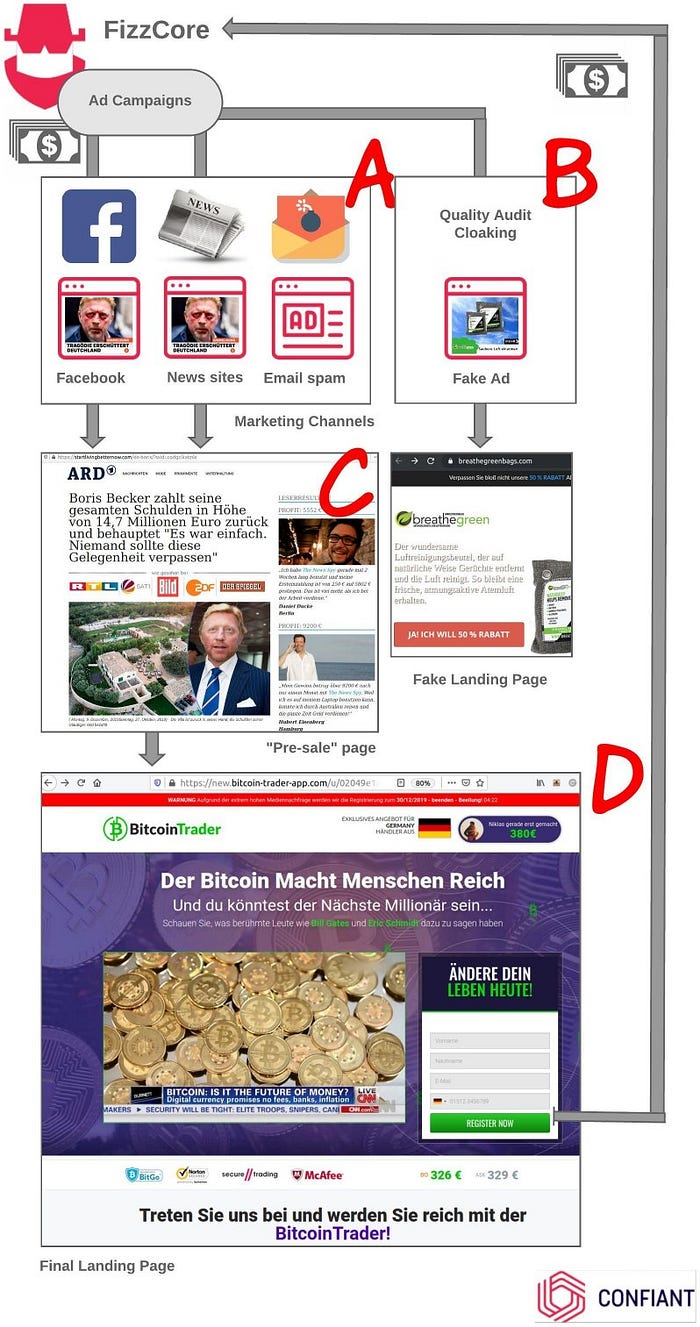
A. Buy ad campaigns to mainstream digital media to reach millions of potential victims. The banner ad presented to users is a click-baity celebrity-related ad with a “shocking” punch line.
B. Embed an unrelated placeholder ad campaign to pass quality audits. These scams are banned from most ad platforms’ policies and would be quickly blocked otherwise.
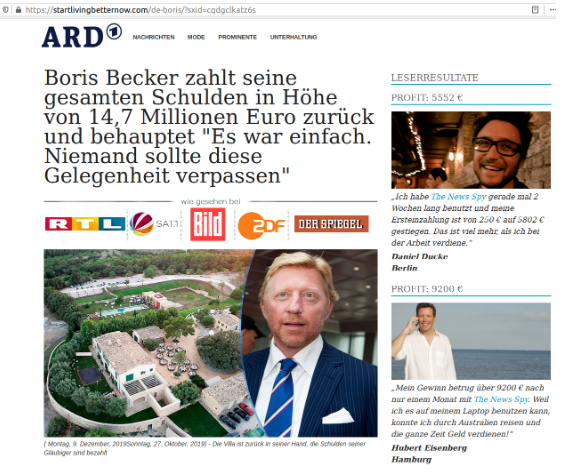
C. The celebrity that was presented in the banner ad now promotes the investment opportunity in a fake editorial style article, carrying some news outlet logo (BBC in the UK, ARD in Germany, Caffeina in Italy, etc…). This so-called “Pre-sale” landing page (in affiliate marketing lingo) is meant to build trust with visitors and prepare for the actual landing page.
D. The actual scam begins. Upon conversion, affiliates like FizzCore receive a hefty commission (varies across affiliate networks but typically a $600 flat rate according to Eric van den Berg’s investigation)
Infrastructure
FizzCore first generation (August 2019)
- Revive Ad Server is an open source ad server that is often used by malvertisers for cloaking purposes.
- UpRival is a small ad serving company based in Utah. It’s unclear what makes UpRival relevant to FizzCore’s use case but it’s certainly been used by FizzCore for cloaking as well. We have notified them of the threat.
FizzCore second generation (November 2019)
FizzCore progressively replaced Revive as “Layer 1" with 3 commercial buy-side ad servers (rotating through them across campaigns).
Additionally, a new custom-made Layer 3 provides stronger cloaking than previous off-the-shelf ad server capabilities, to hide the landing pages from QA efforts. Layer 3 is hosted on a different dedicated domain for every single campaign (see IOCs below).
Evasion techniques
Site copycats
A method typically used by malvertisers (e.g.: AdGholas) is to set up copycat sites with a set of banner ads as a pretext for them to then appear legitimate in the eyes of ad platforms. This technique was favored by FizzCore while iterating on their “First generation” infrastructure.
Here are some examples of FizzCore fake banners and a landing page copycat:
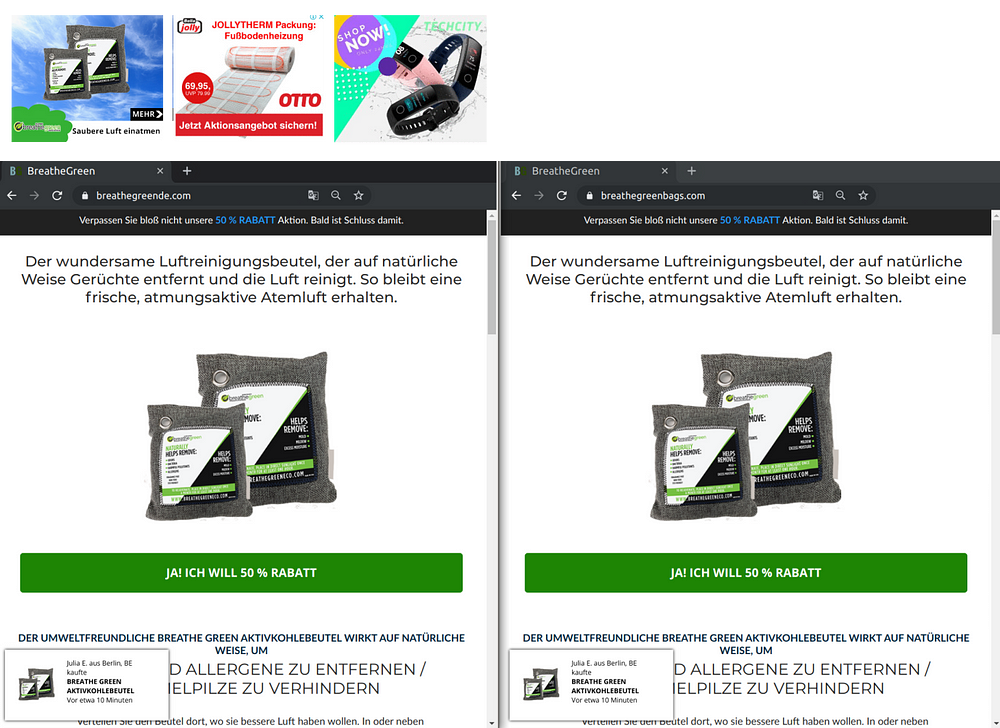
And here’s how the full chain executes in this example:
🡆 Revive Ad server (ad serving first layer)
https://servedby.aqua-adserver.com/afr.php?zoneid=5173&target=_blank&cb=
🡆 Uprival Ad server (second layer): https://api.uprivaladserver.com/v2/a/iframe/?tid=5b943031ba2e541654823f3f&pid=5ddfff05ba2e540b0ce44858&rnd=${TM_RANDOM}&width=300&height=250
🡆 Fake ad creative (BreathGreen for evasion) https://cdn.uprivaladserver.net/images/75cdb8e7-2aa6-4199-a822-745ac6f9db49.jpg
🡆 Actual ad creative (Boris Becker)
https://cdn.uprivaladserver.net/images/d41b9022-95e4-4e8c-958e-5a7c4c20715f.jpg
🡆 On click (same on evasion and on trigger)
https://breathegreenbags.com/
Targeted users in Germany get a 302, others get a 200 on the copycat site.
🡆 ThriveTracker (campaign tracking) — only for targeted users at this point: https://trackrrr.com/path/lp.php?trvid=10231&trvx=a5b4c0a9
🡆 “Pre-sale” landing page Boris Becker bitcoin scam (screenshot in Appendix)
https://startlivingbetternow.com/de-boris/?sxid=cqdgclkatz6s
Here’s another example in the UK. An innocuous advertisement for socks turns into a Paul McCartney bitcoin scam.
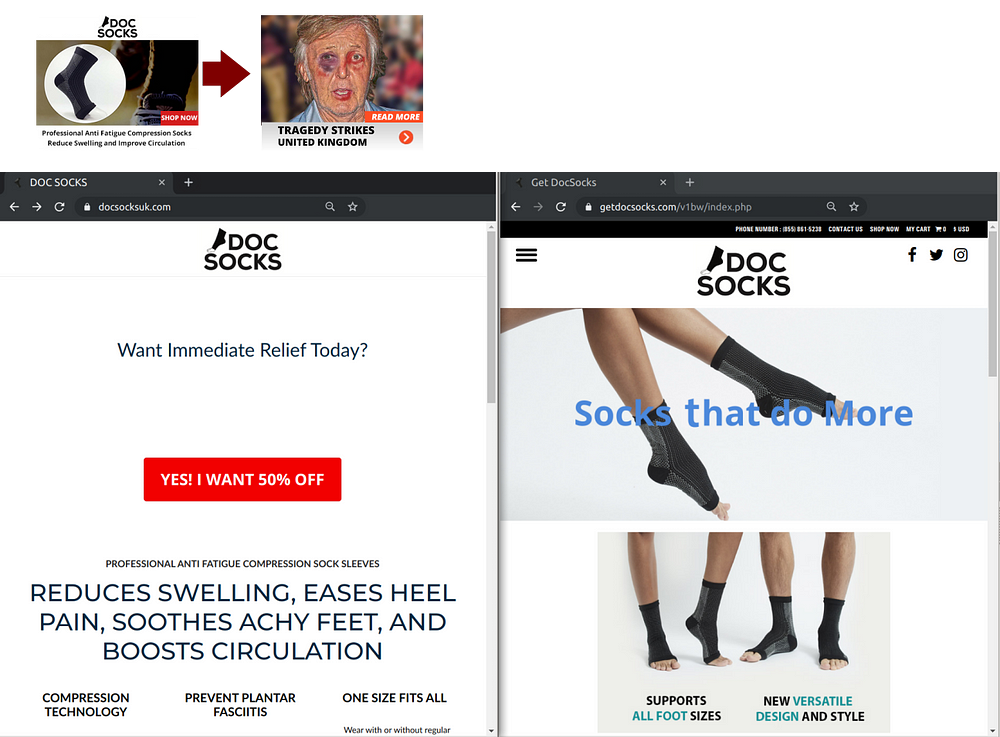
And the full chain execution:
🡆 Ad is initiated by RTBTradeIn, a no-name programmatic ad server:
http://us-nj-e37.rtbtradein[.]com/?t=impr&bwpr=0.3750&uniq=14d856f948531518a642a4d9fad564a1
🡆 Revive Ad server (ad serving first layer)
http://servedby.aqua-adserver[.]com/afr.php?zoneid=5326&target=_blank&cb=
🡆 Uprival Ad server (second layer):
https://api.uprivaladserver[.]com/v2/a/iframe/?tid=5b943031ba2e541654823f3f&pid=5d7ece51ba2e540f7caa927e&rnd=[CACHE-BUSTING-ID-HERE]&width=300&height=250
🡆 Fake ad creative (Doc Sock for evasion)
https://cdn.uprivaladserver[.]net/images/cd0dc7bb-8ed1-45b1-9f6a-f0e662b30fee.jpg
🡆 Actual ad creative (Paul McCartney — link is still up as of this writing)
https://cdn.uprivaladserver[.]net/images/885c952d-7424-4697-a453-09891389266f.jpg
🡆 We didn’t capture the Paul McCartney “Pre-sale” page here 🤷
Abusing commercial adserver targeting
Starting November 2019, FizzCore upgraded their infrastructure (see above “second generation”) and started relying on commercial ad servers to look more legitimate. We spotted 3 different ad serving accounts (we’ve notified the vendors) for which FizzCore paid hefty monthly fees, in lieu of their previous Revive ad server (free and open source, low reputation). Below is an example of this “second generation” execution flow.
🡆 Ad “creative” loads from commercial ad server
https://servedby.flashtalking[.]com/imp/1/119139;4326760;201[…]
🡆 Using the ad server’s targeting capabilities, an additional “cloaked” script loads from:
https://cdn.flashtalking[.]com/xre/432/4326760/2929174/js/j-4326760-2929174.js
🡆 Non-targeted users (e.g. ad scanners, manual QA, etc..) get a different “fake” script at:
https://cdn.flashtalking[.]com/xre/432/4326760/2929107/js/j-4326760-2929107.js
🡆 The cloaked script contains an “extension” that the fake one doesn’t, loading an Iframe at:
https://cdn.flashtalking[.]com/117149/2929174/index.html
For good measure, the cloaked ad server iframe spawns two components:
🡆 One for the image of the creative — an iframe at FizzCore domain postel-kz[.]com (UpRival ad server)
The FizzCore domain will provide one last chance for the image to flip between Cloaked or Fake:

Fake at https://cdn.postel-kz[.]com/images/fa474b69-b04a-40c7-a202-c954b7e241c1.jpg
Cloaked at https://cdn.postel-kz[.]com/images/795a1ad2-9990-45f9-845d-b8b4663b89e0.jpg
🡆 One for the cloaked landing page — the typical FizzCore link cloaker, this time at busetex[.]com.
For the “Fake” ad, it redirects to an unrelated legitimate website, here it’s a RyanAir ad that they borrowed in the wild:
https://www.ryanair.com/flights/de/de/fluege-nach-dublin .
For the “Cloaked” ad, it redirects to the “Pre-sale” page:
We’ve notified the commercial ad servers impacted and they quickly took down the threat actor’s accounts.
Scale
In the ad tech ecosystem
So far, Confiant has detected FizzCore as a buyer on 8 different ad platforms, 4 of which are Tier-1 demand side platforms. FizzCore also obtained access to 3 buy-side ad servers that they progressively leveraged in place of Revive (an open source ad server) to build up legitimacy.
By geography
We have tracked FizzCore across Europe as well as in Oceania:
- Heavily impacted:
United Kingdom, Germany, Italy - Presence detected:
Sweden, France, Spain, Netherlands, Australia, New Zealand
By the numbers
As of this writing, FizzCore is heavily focused on Germany. They’ve had a presence in the country on and off through the last 2 months, with progressively increased scale.
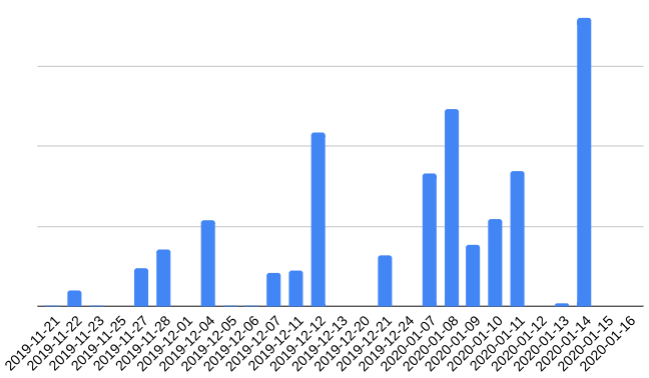
On January 14, 2020, FizzCore served about 14 million shocking celebrity ads on German news sites (based on extrapolated Confiant data).
Standard clickthrough rates in banner ads are abysmal, in the range of 0.01% to 0.1%. By leveraging shocking imagery, FizzCore is able to boost those numbers to up to 3% or more (source: ad industry partners on actual FizzCore campaigns). Let’s look at their performance and ROI using some rough assumptions:
- Views ➡ 14,370,000 (extrapolated from Confiant’s website coverage)
- Clicks ➡ 215,550 (1.5% clickthrough conservative average based on actual ad server data)
- Victims ➡ 2,156 (1% conversion estimate)
- Damage ➡ $6,466,500 ($3,000 average)
- FizzCore net earnings ➡ $1,293,300 ($600 payout)
So, on a big day this is north of $1m net profit in only one country — keeping in mind this is a back-of-the-envelope approximation to get a sense of the magnitude.
Attribution
Who is running FizzCore? How much of the supply chain do they operate?
The Ad Tech Buyer
We have a clear map of the threat actor’s presence on programmatic advertising especially on news websites in Europe. This is what we initially started calling FizzCore.
By working with some trusted partners in the industry a few names kept coming up:
- TomorrowAds: An ad agency with presence in US, Argentina, Spain, Israel
- RevenueLift: Another ad agency with presence in US, Argentina, Spain. It appears to be somehow affiliated with Mango Media Partner, with shared employees and a shared location in Spain. At the time of writing this article, their website had been very recently taken down but can be found on Archive.org (LinkedIn is still up though).
These companies are responsible for buying ad traffic on one side, and obtaining access to commercial ad servers on the other side. We have no additional information on their involvement in the scheme.
The Affiliate
Reviewing tens of different celebrity-endorse “Pre-sale” pages for this bitcoin scam, we were able to associate FizzCore to two domains that are strongly tied to the rest of their infrastructure:
- startlivingbetternow[.]com (Seen in Germany)
- news-now[.]media (Seen in Italy and UK)
Additional evidence is available on inspection of a script on page at https://news-now[.]media/js/tag.js
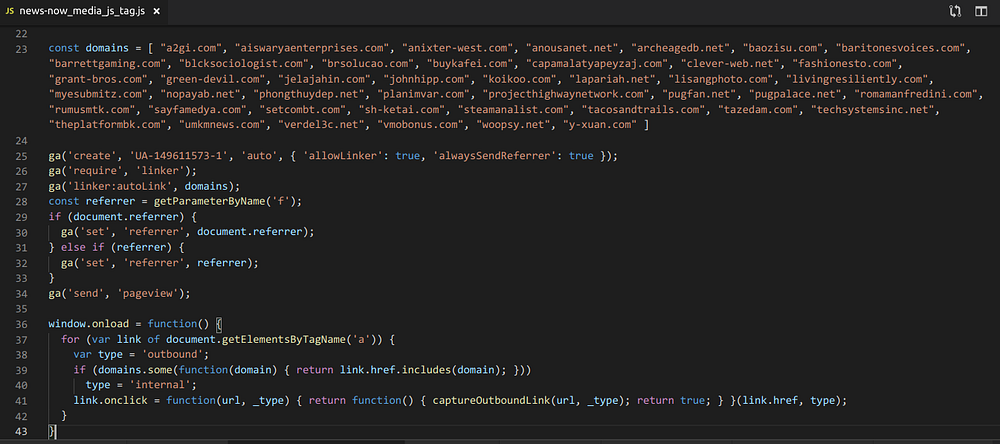
The purpose of this script is to link all these domains for tracking purposes in Google Analytics (learn more about GA’s “linker” feature).
These domains all follow the same patterns and most of them are part of our IOCs from the ad campaigns. This is strong evidence that the ad campaigns and these “pre-sale” pages are operated by the same actor.
Previous FizzCore campaign (May 2019)
Through our investigation, another “Pre-sale” page domain showed up multiple times: presswirenewsday[.]com, especially in Australia, Spain and the Netherlands (see appendix for screenshots and references).
This pre-dates our investigation and we don’t have ad data on it but it uses click-baity banner ads of a different style, photos of government officials juxtaposed with scantily clad women as presented by Steemit in Australia.
Crucially, online advertising blog prebid.blog in May 2019 mentions UpRival as the ad server powering this malicious campaign in Spain. This is a strong tie to our threat actor and the similar modus operandi makes us think that we’re dealing with a previous iteration of FizzCore here.
The Marketer
All elements indicate that the Bitcoin scam is operated by a separate entity that outsources lead generation to affiliates, FizzCore being one of these affiliates.
Conclusion
FizzCore demonstrates how one can successfully leverage ad tech to scale extremely damaging affiliate scams. It’s only the beginning.
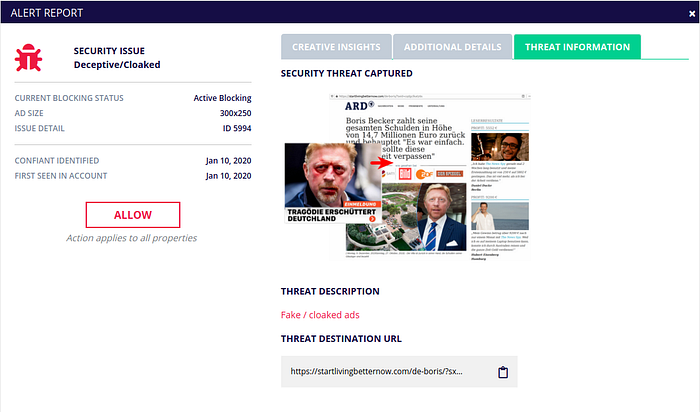
Thanks to its real time malvertising detection engine, Confiant has been able to uncover, track and block this new threat actor. Our solution is constantly helping thousands of online news sites root out the malicious actors and protect their audience.
Confiant users will find this threat categorized as Deceptive/Cloaked in their Dashboard and Alert Log:
Appendices
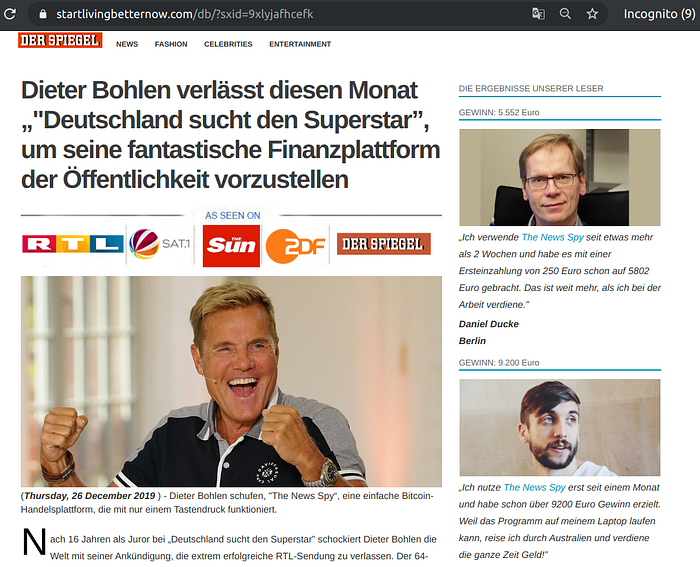
FizzCore’s Celebrity-endorsed bitcoin scam “Pre-Sale” pages
Germany

UK
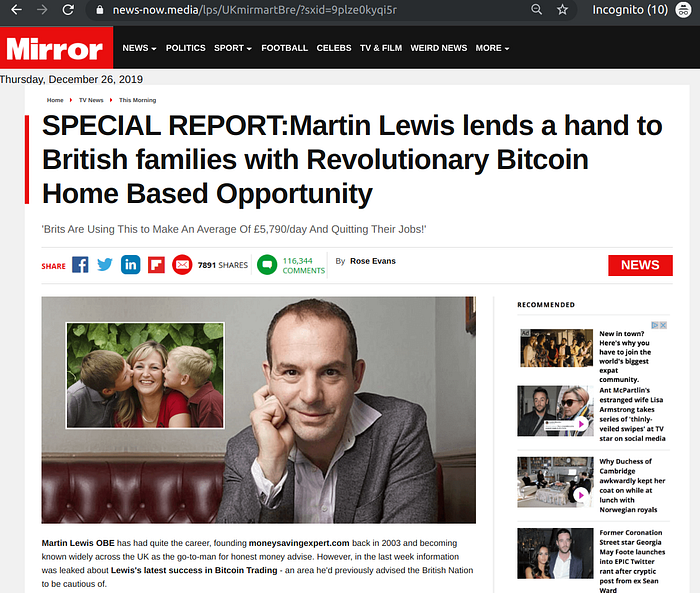
Italy
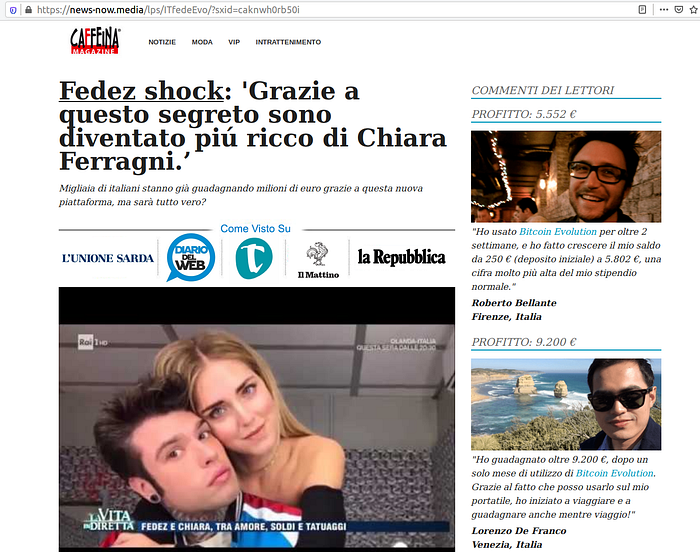
Australia
via Steemit, May 29, 2019
https://presswirenewsday[.]com/twiggyevolution/?sxid=5ueu9fje71ut
Spain
via online advertising blog prebid.blog (May 2019):
https://presswirenewsday[.]com/ES_flopereztwigtemp/?sxid=53s115k4mr8m

Netherlands
presswirenewsday[.]com via Twitter @jaapstronks
Other Bitcoin scam Pre-Sale pages
Not all Bitcoin scams are FizzCore, as they are just one of many affiliates promoting this “campaign”. Here are some examples.
Germany
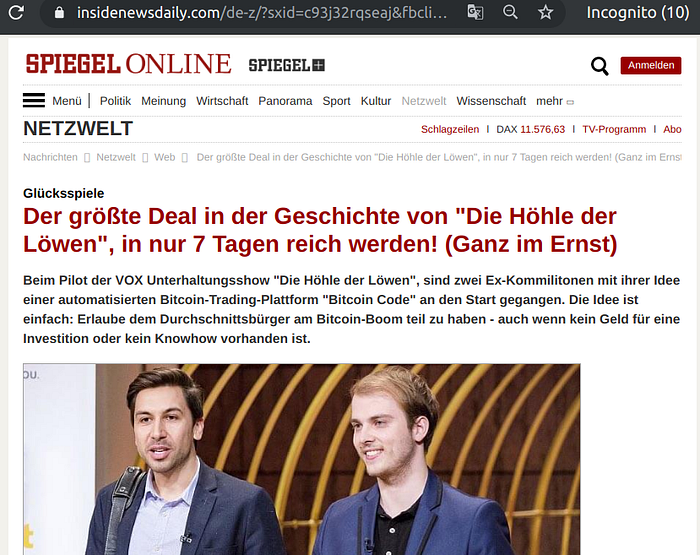
Singapore
Other Celebrity Pre-Sale pages
Fake celebrity endorsements power a large number of scammy affiliation campaigns, not just Bitcoin related ones. Here’s a sampler from the United States.
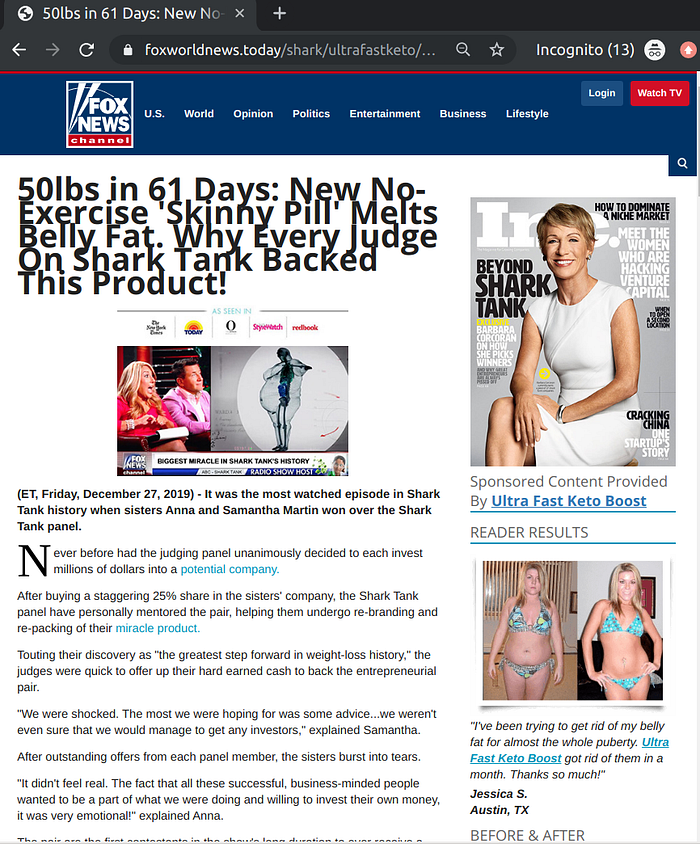
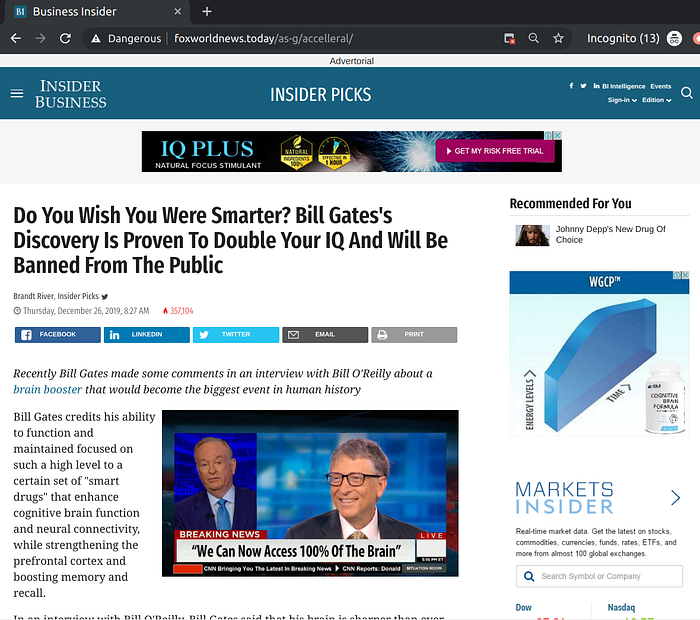
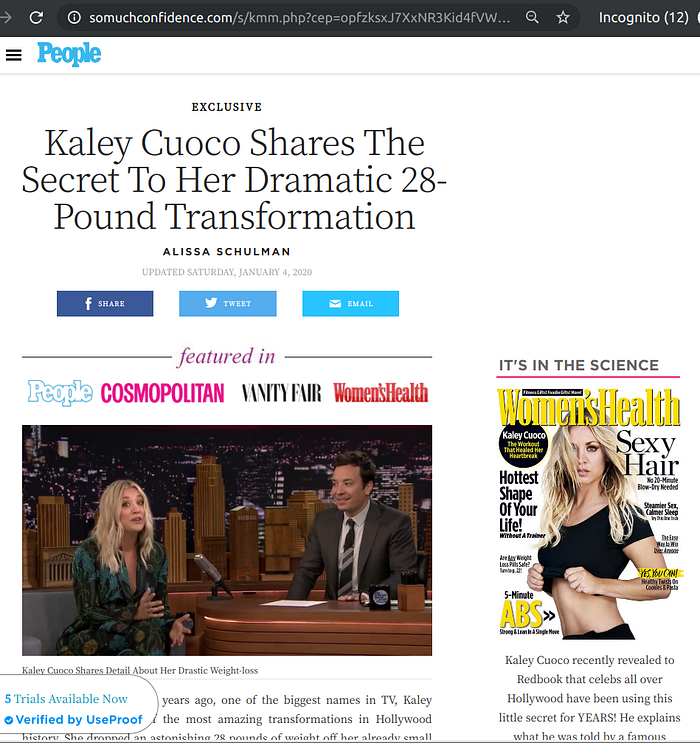
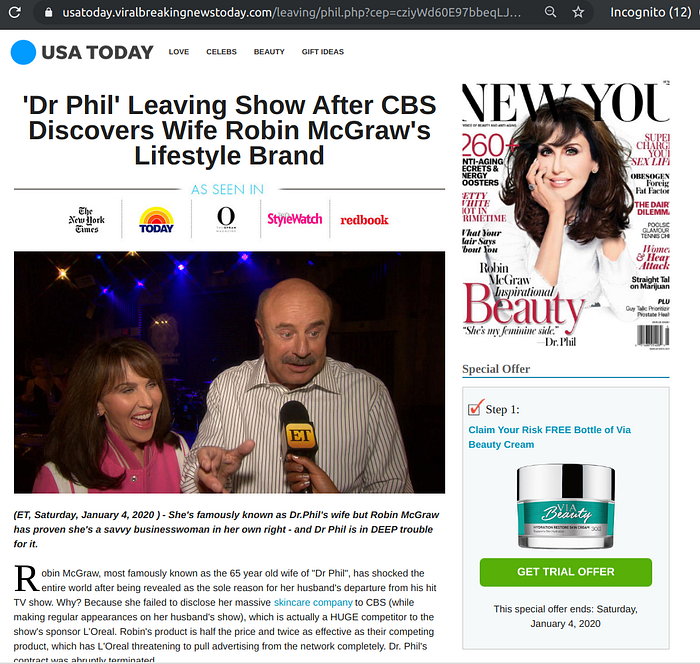
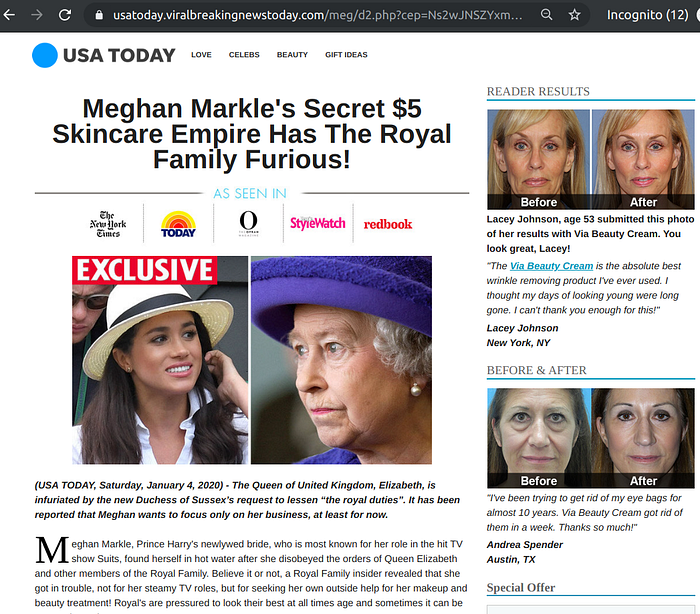
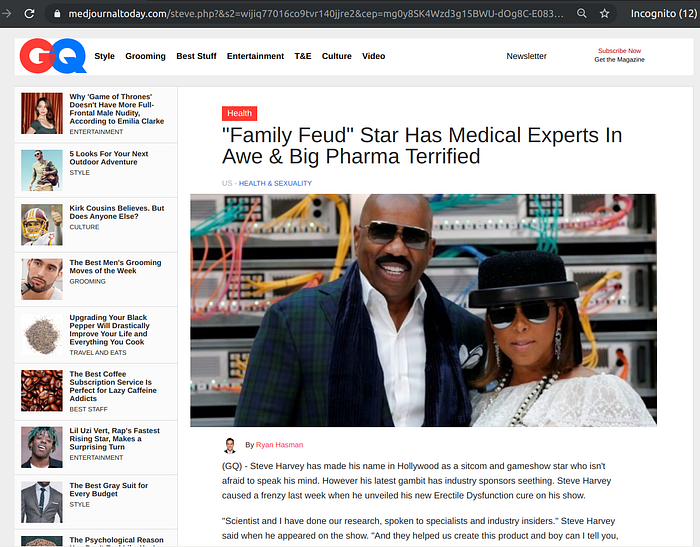
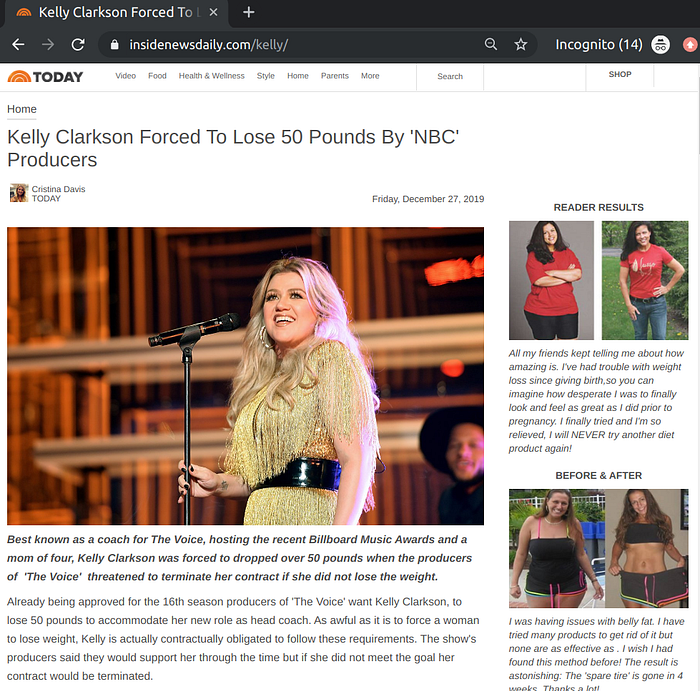
Bitcoin scam landing pages
Here are just a few samples of the actual Bitcoin conversion pages. We’re not aiming for completeness here. All the variants in all languages can be found on Google. Search results are actually stuffed with fake reviews vouching for the service.
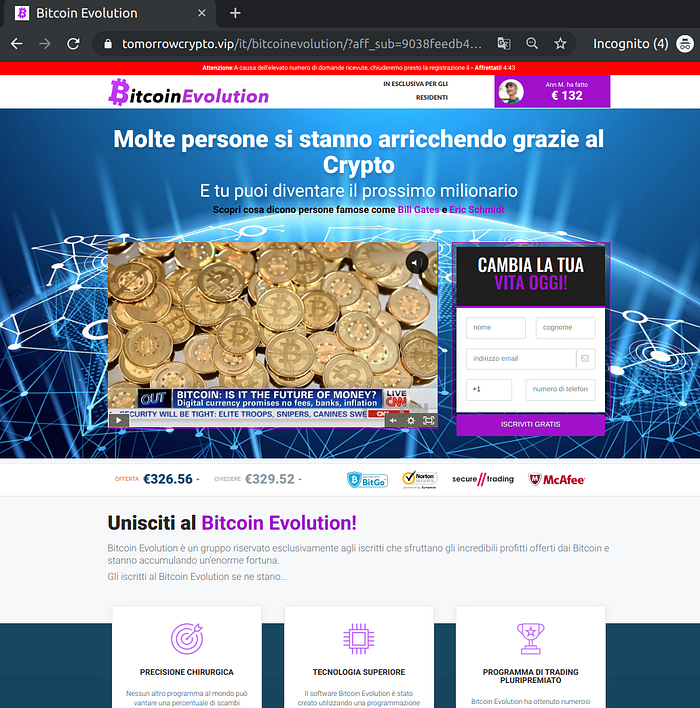

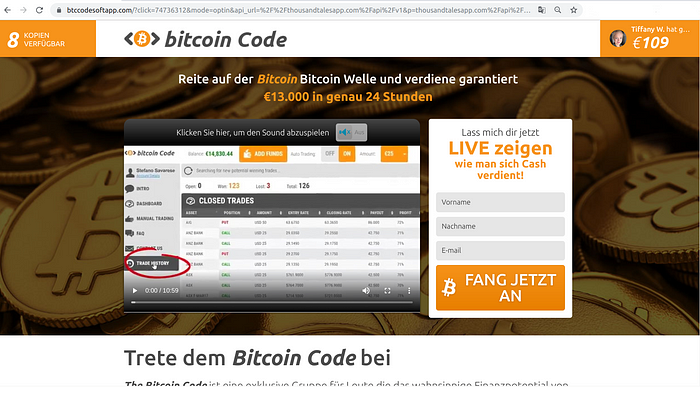
More references
- Excellent deep dive into the world of deceptive affiliate marketing by Jeff White at Palo Alto Networks: Takedowns and Adventures in Deceptive Affiliate Marketing
- ABC News Australia reports on how funds collected from celebrity-endorsed Bitcoin scams are funneled through offshore banks outside of victims’ jurisdictions (Jan 6, 2020).

