
BleepingComputer • 2 minute read
Numerous Sites Leak User E-Mails to Advertising Analytics Services
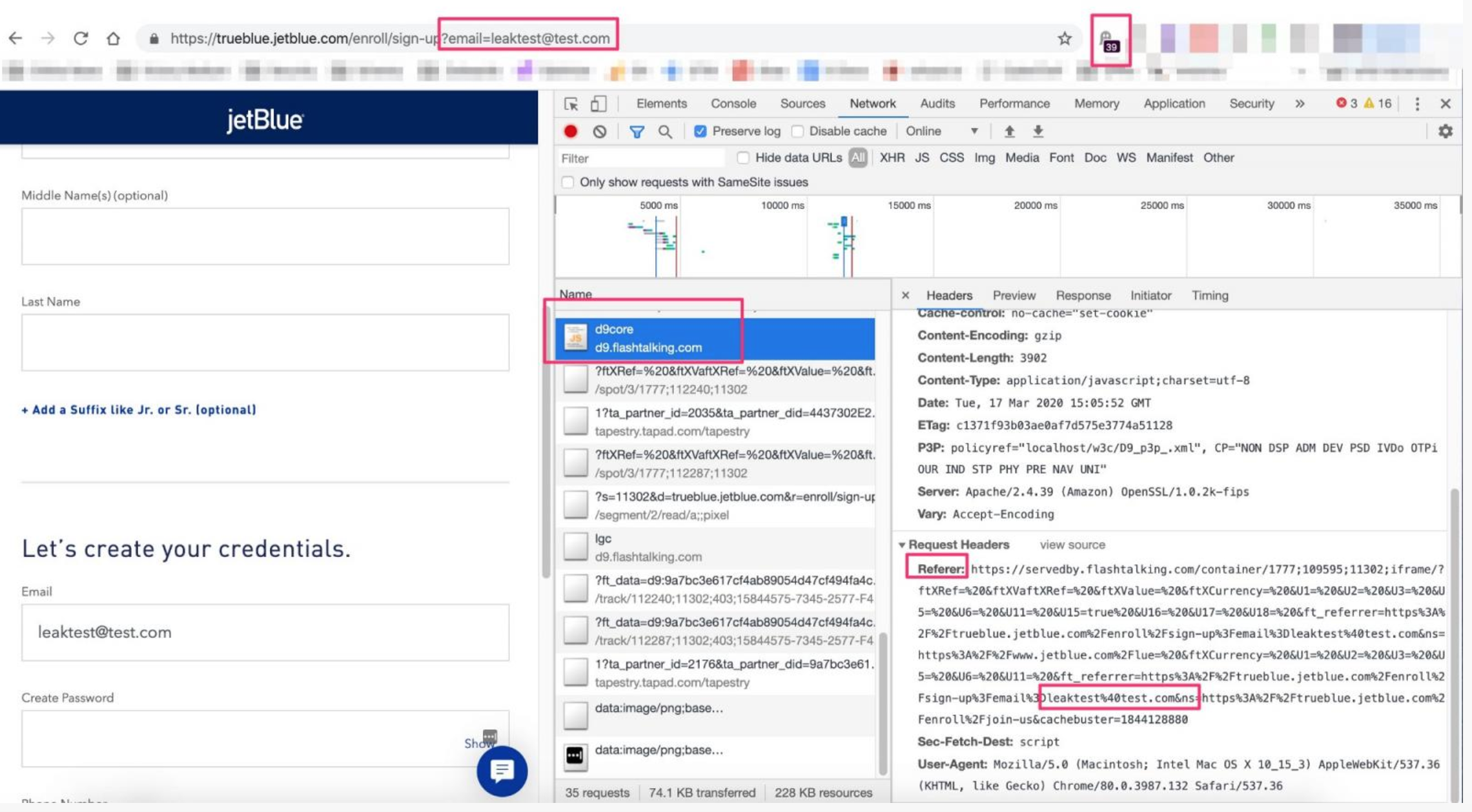
Multiple online services and products are leaking email data belonging to their users to third-party advertising and analytics companies, shows a research published today.
Websites mentioned in the report include Quibi.com, JetBlue.com, KongHQ.com, NGPVan.com, Mailchimp’s Mandrill.com, WashingtonPost.com, Wish.com. Between them, there are hundreds of millions of emails.
Free email addresses
These are not the only ones affected, though; an unknown number is currently leaking this type of data, says Zach Edwards from Victory Medium, a company offering web analytics and testing systems. In some cases, email data is leaked to dozens of such service.
On the list of parties receiving email information are major services providing analytics, advertising, tracking, optimization, and marketing instruments, like Google, Facebook, Twitter, Mixpanel, Wistia, Pardot, CrazyEgg, New Relic, DrawBridge.
Edwards pinned the issue to improper setup of marketing analytics systems, which could receive user email addresses from email systems, user signup or unsubscribe flows.
“When any 3rd party Javascript code loads on a website, metadata from the user and the website can be transmitted to the 3rd party domain / company that controls that code”
The details are passed in request headers through a web browser and can be anything from a page the user visited to their location, type of device used, or other forms of information: fingerprinting, cookies, URL query string or parameters.
Edwards points that says that passing email data in a URL bar through JavaScript can be prevented by using ad blockers. This could also happen by default in Safari, Brave, and Firefox browsers. But not in Google Chrome, where users have to explicitly disable JavaScript.
In some cases, email data leaked this way was passed in plain text while in other instances the simple base64 encoding was used, so protection was only on the surface.
Edwards calls the leaks data breaches, since email addresses count as personal information and is, therefore, protected through regulations and laws in many countries.
Creating new account? URL gets your email
In his report today, the researcher provides several scenarios that leaked users’ emails to various third-party services through JavaScript code that collects data from a website.
One example is Quibi short-form mobile video platform, which passes a new user’s email when they click on the confirmation link for setting up an account.
“When a user clicks this email confirmation link, their email address is appended into the URL they are clicking in plain text, and sent to 3rd party advertising and analytics companies”
The company received a report on April 17 but a human found the memo only recently and just started dealing with the problem, Edwards told BleepingComputer. Apparently, they made some changes to fix the problem. We reached out to Quibi but received no reply at publishing time.
Below you can see how a new user’s plain text email address transpires in the URL and how it passes to SnapChat’s and Twitter’s ad endpoints. When tested, other endpoints belonging to Google, Facebook, CivicUK, LiveRamp, SkimAds, Tapad, picked the user data, too.
Another company leaking base64-encoded user email, was Wish.com, Edwards found. The data went to at least Google, Pinterest, Facebook, Criteo, PayPal, and Stripe.
The researcher says that once he informed the organization of the issue, they managed to rebuild their email infrastructure and launch a new auto-login flow via email. They did this in an impressive time, 72 hours.
Eliya Stein of Confiant confirmed what Edwards had discovered on Wish.com, saying that subscribers that clicked a link in a marketing email had their address leaked to a third party. He commented:
“From my observations, it looks like these are mostly tracking endpoints and not actual ad slots on these pages. If they ever introduce display ads connected to rtb on these pages, then the impact of this leak has the potential to be quite large”
Read Complete Article: https://www.bleepingcomputer.com/news/security/numerous-sites-leak-user-emails-to-advertising-analytics-services/



