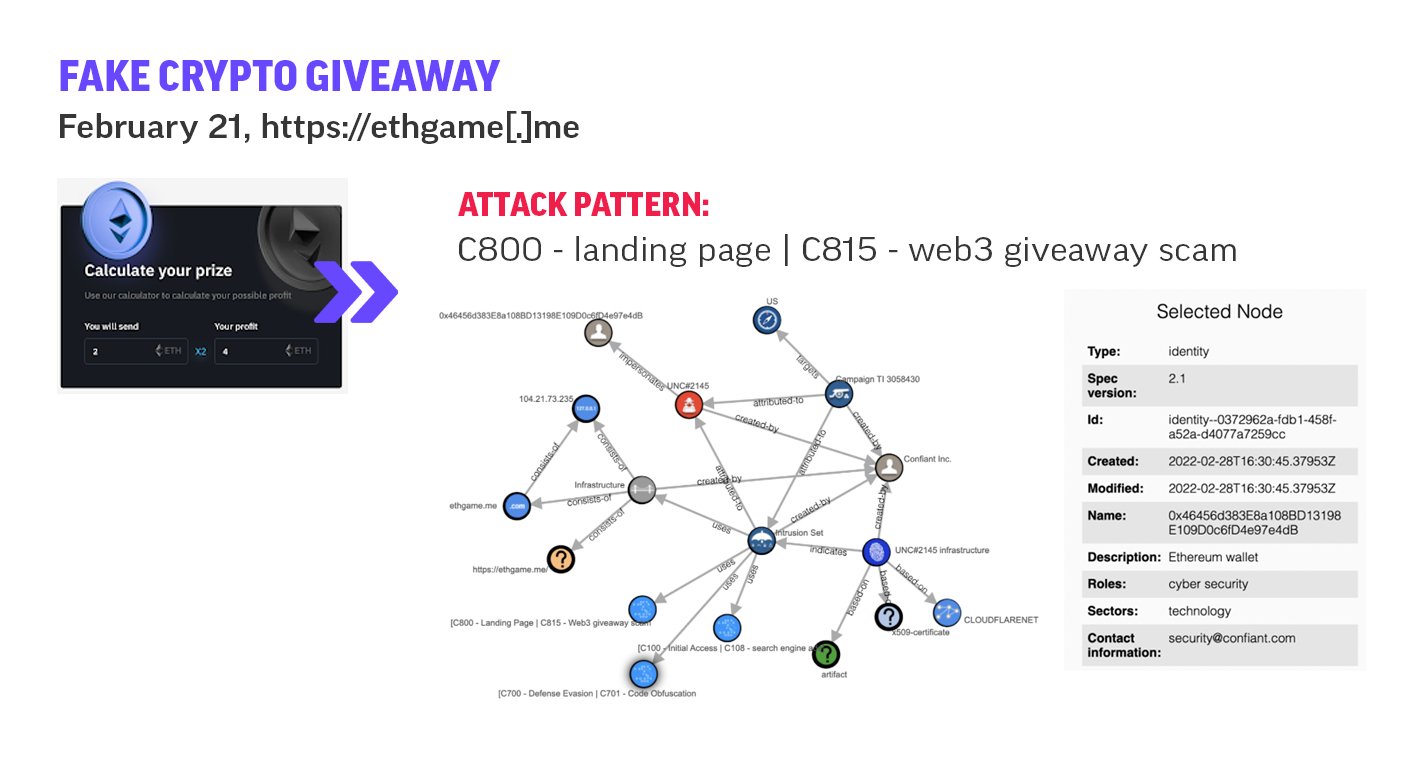
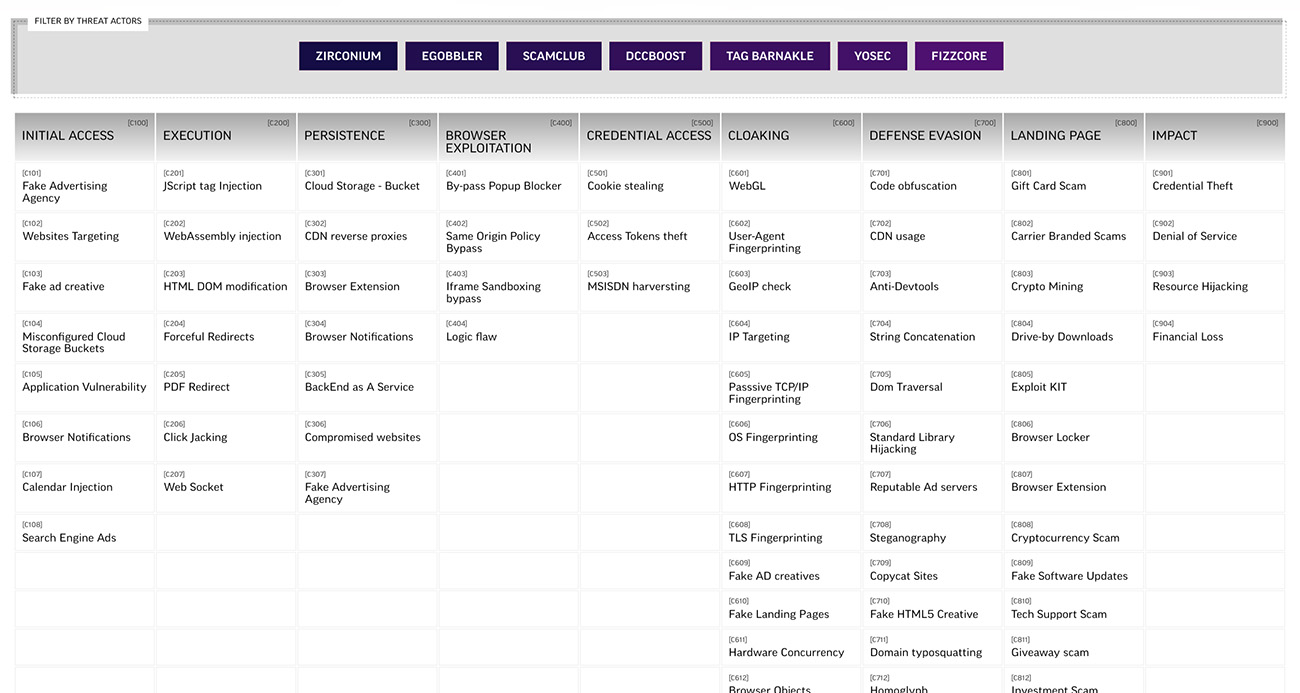
First created in October of 2021, Confiant’s Malvertising Attack Matrix is modeled on the fabled MITRE ATT&CK® and encompasses 80+ techniques, 7 threat actors, 20 UNCs and +200 clusters of Malvertising activity currently using ads as a vector to target users throughout their daily online activities with all the precision and efficiency that the ad tech world has to offer.
Updated in March of 2022 to include Web3 specific attacks, this knowledge base of the tactics, techniques and attackers is provided in service to raising the knowledge of this previously unmapped vector amongst the cyber security community. Ads are a trusted medium and the acceleration of the digital ad industry over the past ten years has created a formidable risk vector for users both personally and professionally. All of Confiant’s Threat Intel integrates the Malvertising Attack Matrix.