Multiple massive malvertising attacks which targeted iOS users from the U.S. and multiple European Union countries for almost a week used a Chrome for iOS vulnerability to bypass the browser's built-in pop-up blocker.
eGobbler, the threat group behind the flurry of attacks, used "8 individual campaigns and over 30 fake creatives" throughout their push, with each of the fake ad campaigns having lifespans of between 24 and 48 hours.
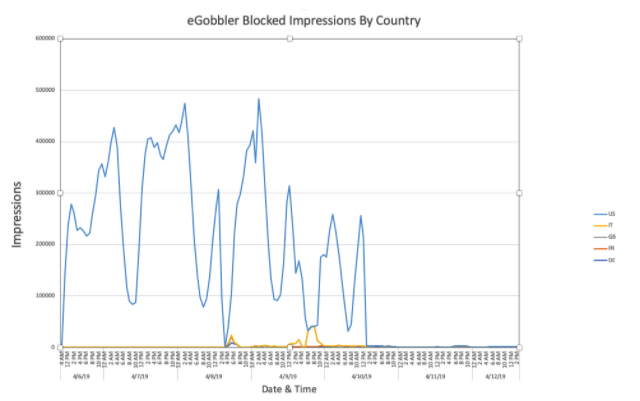
In total, according to the Confiant researchers who discovered and monitored eGobbler's iOS-targeted attacks, roughly 500 million users sessions were exposed to this large scale orchestrated campaign pushing fake ads.
eGobbler's campaigns usually stay active for a maximum of 48 hours, immediately followed by short periods of hibernation which abruptly end when the next attack starts as discovered by Confiant's experts.
The April campaign used landing pages hosted on .world domains and it made use of pop-ups to hijack users sessions and redirect the victims to malicious landing pages.
While using pop-ups has been observed before as part of similar campaigns as the method used to redirect targets to pages designed by the malicious actors for phishing or malware dropping purposes, it's definitely an unusual one considering the effectiveness of browser pop-up blockers.
The crooks' decision to use pop-ups to hijack users sessions was revealed after the researchers tested the malvertising campaign's payloads "across over two dozen devices, both physical and virtual" and "split test this experiment between sandboxed and non-sandboxed iframes."
Read Complete Article: https://www.bleepingcomputer.com/news/security/malvertising-campaign-abused-chrome-to-hijack-500-million-ios-user-sessions/