
Confiant Threat Intelligence Team • 4 minute read
ScamClub Threat Intelligence Report Overview

UPDATE: On September 27, 2023, Motorik contacted us to validate our discoveries, affirming that they had ceased their collaboration with Waytopmobi earlier in the year. We have also detected and confirmed, through our telemetry, the presence of DecenterAds, an advertising platform directly linked to ScamClub.
Threat Actor Ownership Exposed
This strategic threat intelligence report details the activities of threat actor ScamClub during Q1 and Q2 of 2023. For the first time, we identify the entity behind ScamClub operations. The report aims to provide insights into the threat landscape and its implications for the ad tech industry, particularly focusing on the interests of DSPs and SSPs.
- ScamClub is a persistent and serious threat to SSPs, DSPs, walled gardens, and publisher reputations because they use ad platforms to target viewers with financial scam attacks.
- Confiant threat intelligence team has linked the operations and ownership to one entity: Way Top International Advertising LTD, Hong Kong.
- ScamClub generated an estimated $8.5 million in total revenue for the first two quarters of 2023. (This revenue figure was determined solely from the cc-submit CPA model, utilizing a conversion rate of 0.05% and an average of $20 per conversion for tier-1 countries.)
- ScamClub attacks have negative repercussions on DSP, SSP, and Publisher brand reputations. In Q1 and Q2 of 2023, a total of 31 SSPs and 12 DSPs were affected by these escalating ScamClub attacks.
Key Findings
During the reporting period, ScamClub exhibited a significant escalation in its activities, posing a substantial risk to the entire ad tech ecosystem, including DSPs, SSPs, and publishers. The primary motivation behind ScamClub's actions remains financial gain, as they target the ad tech industry to engage in illicit and exploitative activities. Confiant's Threat Intelligence team detected two ongoing ScamClub campaigns, with the first campaign accounting for 80% of the attack volume and displaying a consistent upward trend. Based on Confiant's internal telemetry, infrastructure tracking, and observations over time, the threat actor behind ScamClub was attributed with high confidence to an entity named WayTop International Advertising Limited registered in Hong Kong by a Chinese individual. WayTop International has been orchestrating ScamClub operations since at least 2019.
ScamClub, operating as a threat actor, exemplifies the traits of a well-organized, highly skilled, and well-financed professional entity that often collaborates in teams to execute their operations. They display advanced capabilities, demonstrating their expertise in developing unique programs and codes to target various operating systems, web browsers, and advertising technology software. With an in-depth knowledge of web browsers, programming languages, and infrastructure topologies, ScamClub prioritizes operational security while conducting their activities. Their significant contributions involve the discovery of 0-day browser vulnerabilities and the pioneering of novel attack techniques, establishing their reputation as innovators within the cyber threat landscape.
Starting from January 2023, Confiant has been closely monitoring the significant rise in ScamClub's activities. The entire ad tech industry, including DSPs and SSPs (Supply-Side Platforms), witnessed a notable surge in ScamClub attacks.
Throughout Q1 and Q2 of 2023, a total of 31 SSPs and 12 DSPs were affected by these escalating ScamClub attacks, posing challenges to the overall ad tech landscape.
According to the estimates from our strategic threat intelligence report, ScamClub generated approximately $8.5 million in total revenue for the first two quarters of 2023. This revenue figure was determined solely from the cc-submit CPA model, utilizing a conversion rate of 0.05% and an average of $20 per conversion for tier-1 countries.
A ScamClub attack has significant repercussions on DSPs, SSPs, and Publisher websites. DSPs may suffer reputation damage and client loss, while SSPs may lose publisher trust and experience revenue decline. Ad Exchanges might face financial losses, legal issues, and regulatory challenges. Publisher websites can lose user trust and suffer reduced ad revenue due to user safety concerns. To address these impacts, robust security measures, collaborative efforts, and regular audits are necessary to ensure a safer online advertising ecosystem for all stakeholders .
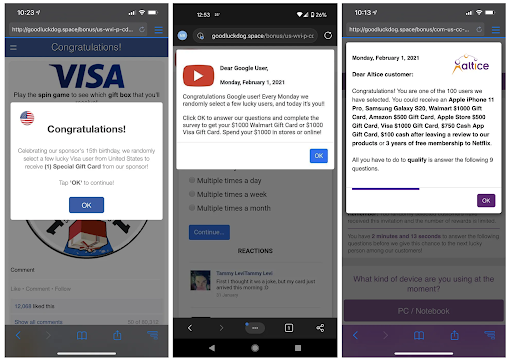
ScamClub Visa landing page example, Source: Confiant
Recommendations
A malvertising attack can have significant impacts on DSPs (Demand-Side Platforms), SSPs (Supply-Side Platforms), ad exchanges, and publisher websites. Here are the potential impacts on each of these entities:
DSPs (Demand-Side Platforms)
- Reputation damage: DSPs may suffer reputational harm if their ad inventory is associated with malicious ads. Advertisers may lose trust in the platform's ability to deliver safe ad placements.
- Client loss: Advertisers might withdraw from using the DSP due to concerns about their ads being associated with malicious content, leading to revenue loss for the platform.
- Increased scrutiny: Following an attack, DSPs may face heightened scrutiny from industry authorities, leading to potential regulatory challenges.
SSPs (Supply-Side Platforms)
- Loss of publisher trust: If a malvertising attack originates from an SSP, publishers may lose confidence in the platform's ad serving capabilities, leading to a reduction in the number of publishers willing to work with them.
- Revenue decline: SSPs may experience reduced demand for their ad inventory if advertisers are wary of the platform's security practices, resulting in decreased revenue for the SSP.
Ad Exchanges
- Financial losses: Ad exchanges may face financial losses due to fraudulent ad clicks or impressions generated by malicious ads, impacting their advertising ROI.
- Legal and regulatory issues: Ad exchanges might face legal repercussions if the malvertising attack leads to harm to users or advertisers. They may be held responsible for not adequately filtering and preventing malicious content.
Publisher Websites
- User trust erosion: Users visiting infected publisher websites may have their trust eroded, impacting the site's reputation and long-term traffic.
- User safety concerns: Malicious ads can lead to users being exposed to malware, phishing attempts, or scams, which can result in personal and financial damage to users.
- Reduced ad revenue: Publishers may experience reduced ad revenue if advertisers avoid placing ads on their website due to security concerns.
To mitigate the impact of malvertising attacks, the involved parties should implement robust security measures, including stringent advertiser vetting processes, regular security audits, and maintaining up-to-date cybersecurity solutions. Collaborative efforts between DSPs, SSPs, ad exchanges, and publishers are essential to combat malvertising and ensure a safer online advertising ecosystem.
Conclusion
Throughout the first and second quarters of 2023, ScamClub's activities have reaffirmed as a noteworthy and ever-changing menace to the ad tech industry. However, DSPs and SSPs can effectively counter this threat by comprehending ScamClub's tactics, techniques, and procedures (TTPs) as well as indicators of compromise (IOCs). Taking a proactive approach to cybersecurity, these platforms can fortify their defenses, mitigate potential damages, and play a crucial role in fostering a more secure ad tech ecosystem.
Read the technical article on Medium, learn more about "ScamClub’s Deceptive Landing Pages" in our follow-up article, or download the full report below:



